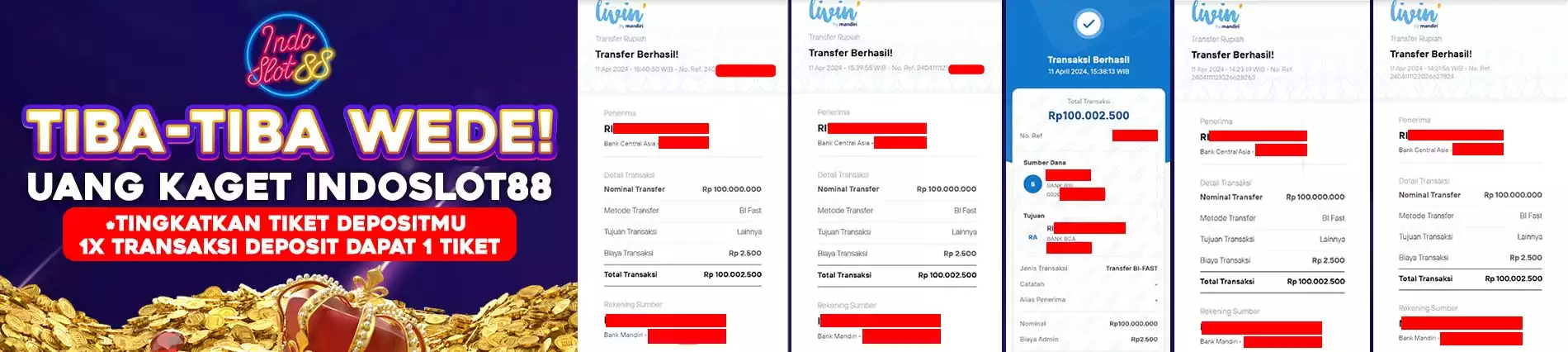
IDR
Layanan Member
Tambah Dana
Waktu
Menit
WITHDRAW
Waktu
Menit
Sistem Pembayaran

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

OFFLINE

OFFLINE

ONLINE

ONLINE

OFFLINE

OFFLINE

ONLINE

ONLINE

ONLINE

OFFLINE

ONLINE

OFFLINE

OFFLINE

OFFLINE

OFFLINE

OFFLINE

ONLINE

ONLINE

ONLINE
INDOSLOT88 || MAINKAN SEKARANG PLATFORM TERBAIK EASY JACKPOT